Sql Vulnerability Scanner
Posted : admin On 02.10.2019SQL Vulnerability Assessment. 4 minutes to read.In this articleAPPLIES TO: SQL Server Azure SQL Database Azure SQL Data Warehouse Parallel Data WarehouseSQL Vulnerability Assessment is an easy to use tool that can help you discover, track, and remediate potential database vulnerabilities. Use it to proactively improve your database security.Vulnerability Assessment is supported for SQL Server 2012 and later, and can also be run on. Vulnerability Assessment featuresSQL Vulnerability Assessment (VA) is a service that provides visibility into your security state, and includes actionable steps to resolve security issues and enhance your database security. It can help you:. Meet compliance requirements that require database scan reports.
Meet data privacy standards. Monitor a dynamic database environment where changes are difficult to track.The VA service runs a scan directly on your database. The service employs a knowledge base of rules that flag security vulnerabilities and highlight deviations from best practices, such as misconfigurations, excessive permissions, and unprotected sensitive data. The rules are based on Microsoft's recommended best practices, and focus on the security issues that present the biggest risks to your database and its valuable data. These rules also represent many of the requirements from various regulatory bodies to meet their compliance standards.Results of the scan include actionable steps to resolve each issue and provide customized remediation scripts where applicable. An assessment report can be customized for your environment, by setting an acceptable baseline for permission configurations, feature configurations and database settings. PrerequisitesThis feature is only available on SQL Server Management Studio (SSMS) v17.4 or later.

Please make sure you are using the latest version. You can find the latest version. Getting startedTo get started with running a Vulnerability Assessment on your database, follow these steps:.Open SQL Server Management Studio.Connect to an instance of the SQL Server Database Engine or localhost.Expand Databases, right-click a database, point to Tasks, select Vulnerability Assessment, and click on Scan for Vulnerabilities.You can run a scan that checks for server-level issues by scanning one of the system databases.
Expand System Databases, right-click the master database, point to Tasks, select Vulnerability Assessment, and click on Scan for Vulnerabilities.TutorialUse the following steps to run and manage vulnerability assessments on your databases. Run a scanThe Scan For Vulnerabilities dialog allows you to specify the location where scans will be saved. You can leave the default location or click Browse. To save the scan results to a different location.When you are ready to scan, click OK to scan your database for vulnerabilities. NoteThe scan is lightweight and safe. It takes a few seconds to run, and is entirely read-only.
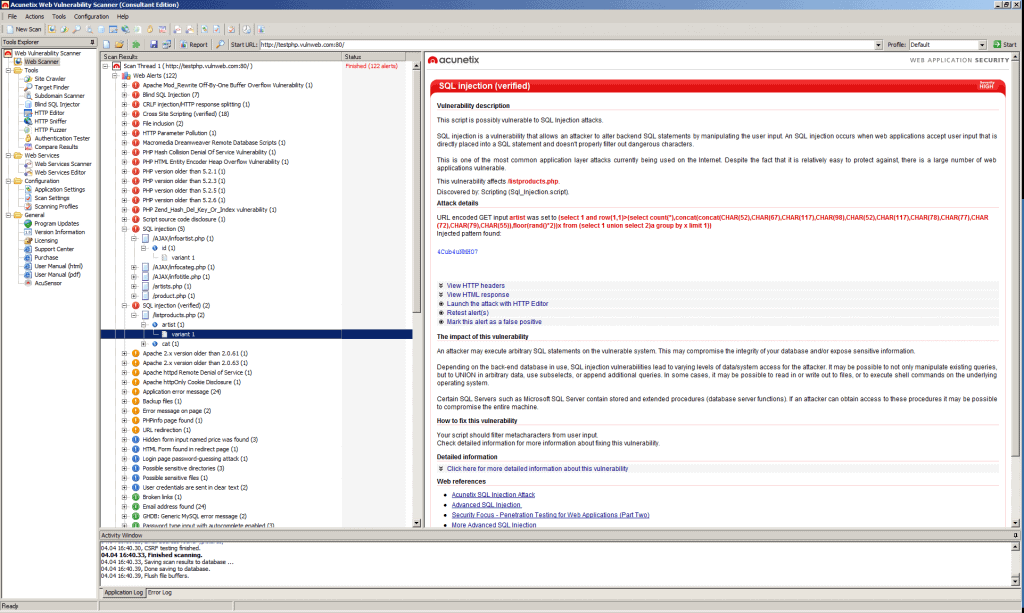
This cloud-based service serves as a SQL injection scanner and can perform a lightweight scan to find critical vulnerabilities and prioritize your greatest risks. Acunetix web vulnerability scanner is a free to download online tool, which can scan websites for security issues. Why it is on the rise? As mentioned earlier that web security at the application level is the most overlooked aspect of security, so hackers exploit it.
It does not make any changes to your database.2. View the reportWhen your scan is complete, your scan report is automatically displayed in the primary SSMS pane. The report presents an overview of your security state; how many issues were found, and their respective severities. Results include warnings on deviations from best practices, as well as a snapshot of your security-related settings, such as database principals and roles and their associated permissions. The scan report also provides a map of sensitive data discovered in your database, and includes recommendations of the built-in methods available to protect it.3. Analyze the results and resolve issuesReview your results and determine which findings in the report are true security issues in your environment. Drill-down to each failed result to understand the impact of the finding, and why each security check failed.
Vulnerability Scanner Definition
Wireless Security Tool
Use the actionable remediation information provided by the report to resolve the issue.4. Set your BaselineAs you review your assessment results, you can mark specific results as being an acceptable Baseline in your environment. The baseline is essentially a customization of how the results are reported. Results that match the baseline are considered as passing in subsequent scans.Once you have established your baseline security state, VA only reports on deviations from the baseline, and you can focus your attention on the relevant issues.5.
Run a new scan to see your customized tracking reportAfter you complete setting up your Rule Baselines, run a new scan to view the customized report. VA now reports only failing security issues that deviate from your approved baseline state.6. Open a previously run scanYou can view the results of previously run Vulnerability Assessments at any time by opening an existing scan. Do so by right-clicking a database, pointing to Tasks, selecting Vulnerability Assessment, and clicking on Open Existing Scan.
Select the scan results file you would like to view and click Open.You can also open an existing scan result via the File-Open menu. Select Vulnerability Assessment. And open the scans directory to find the scan result you wish to view.VA can now be used to monitor that your databases maintain a high level of security at all times, and that your organizational policies are met. If compliance reports are required, VA reports can be helpful to facilitate the compliance process.
Sql Vulnerability Assessment
Manage Vulnerability Assessments using PowerShellYou can use PowerShell cmdlets to programmatically manage Vulnerability Assessments for your SQL Servers. The cmdlets can be used to run assessments programmatically, export the results and manage baselines.To get started, download the latest from the PowerShell Gallery site. You can learn more. Next stepsLearn more about SQL Vulnerability Assessment using the following resources:.Feedback.